As organisations in Europe increasingly scale their cloud usage, one challenge consistently emerges: how to monitor and audit activity across hundreds of AWS accounts in a cost-efficient, real-time, compliant way.
For enterprises under strict EU regulatory regimes — GDPR, financial-sector auditability, internal risk controls — the need for unified logging and monitoring is critical.
Recently, we supported a large EU enterprise facing exactly this problem. With 270 AWS accounts spread across multiple business units, they needed a centralised, scalable, and low-cost solution to collect logs, detect suspicious actions, and maintain compliance — without introducing operational overhead or expensive infrastructure.
Inspired by the AWS architecture described in “Enhancing Multi-Account Activity Monitoring with Event-Driven Architectures” on the AWS Blog, we designed a serverless, event-driven logging pipeline that solved all of these challenges.
The Customer’s Challenge
The organisation’s security and compliance team required:
- Complete visibility of all API activity across 270 AWS accounts
- Real-time alerting for IAM changes, privilege escalations, and sensitive configuration updates
- A single, centralised audit trail for GDPR, internal audits, and regulatory reporting
- A cost-efficient model — avoiding the high expense of polling API activity or running heavy SIEM ingestion
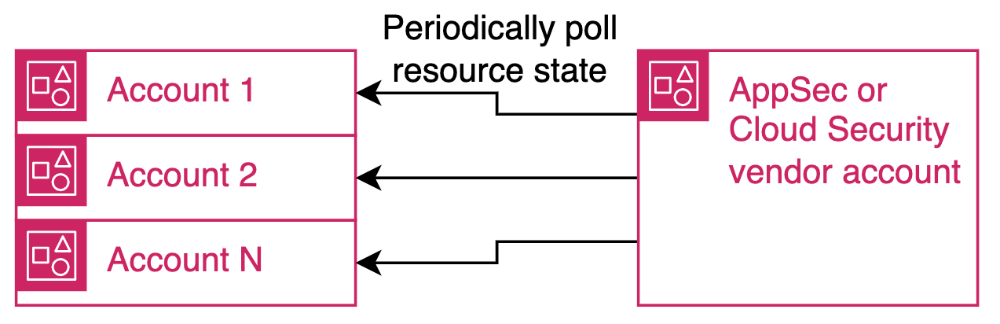
The existing approach — periodic polling and manual auditing — was slow, expensive, and missed activity happening between polling windows. As the number of accounts grew, this method was no longer viable.
Our Solution: Event-Driven Multi-Account Monitoring
We implemented a centralised logging and monitoring solution across all 270 AWS accounts using CloudTrail, AWS Organizations, and EventBridge — using a push-based architecture rather than resource-intensive polling.
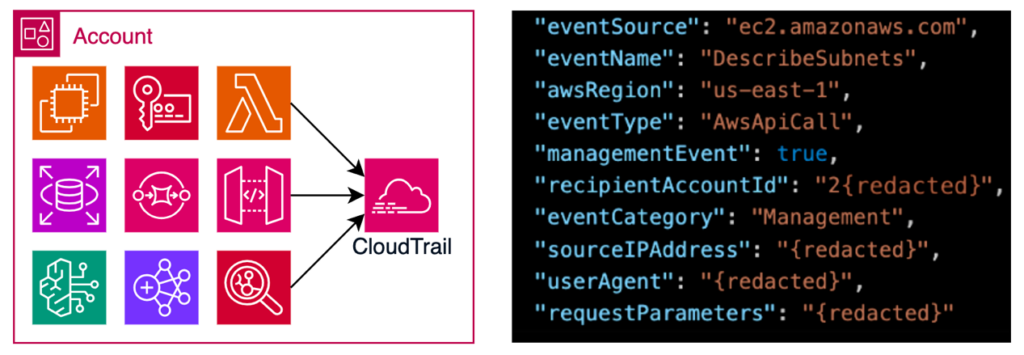
1. Distributed Activity Capture (Per Account)
In each AWS account:
- AWS CloudTrail collects all API actions across 250+ AWS services
- EventBridge filters and routes relevant events
- Only required activity (IAM changes, API calls, security-sensitive events) is delivered to a central audit account
This ensures minimum noise and maximum cost efficiency.
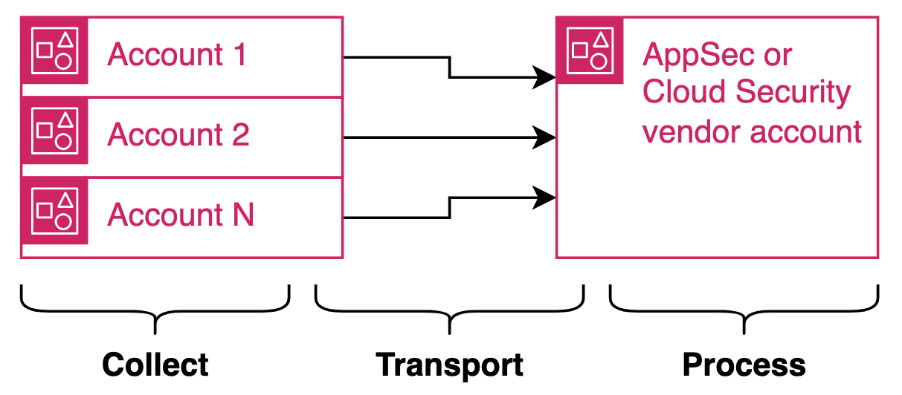
2. Event-Driven Transport (Push Model)
Instead of running scheduled scanners or pulling logs via API, each account pushes events automatically to central accounts.
This event-driven pattern provides:
- Milliseconds-to-seconds latency
- Guaranteed delivery
- Zero infrastructure to manage
- Significantly lower cost than polling services
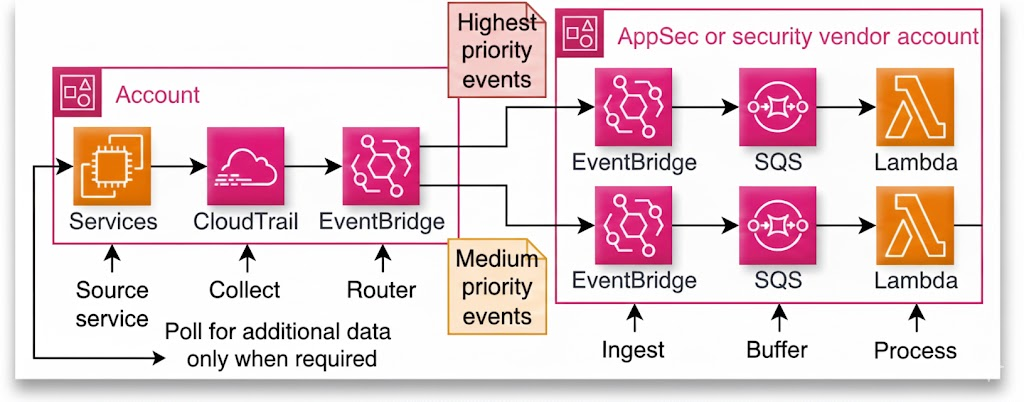
3. Centralised Aggregation & Processing
In the central audit/compliance account, we built a unified pipeline where:
- EventBridge receives cross-account logs
- SQS buffers traffic and prevents throttling
- Lambda & Kinesis perform real-time processing
- All data is delivered into a secure S3 Data Lake
- Optional: enrichment into OpenSearch or external SIEMs
By classifying events early, high-risk actions (e.g., IAM privilege updates) are processed in real time, while lower-priority events are batched for cost savings.
Results for the Customer
✔ Full Compliance & Audit Readiness
The organisation now has complete, centralised visibility of all API activity — supporting GDPR audit trails, internal investigations, and compliance reporting.
✔ Real-Time Risk Detection
IAM modifications, privilege escalations, unusual logins, and resource configuration changes trigger instant notifications.
✔ Highly Cost-Efficient
Because the solution is fully serverless and event-filtered:
- No EC2 or polling systems to run
- No over-provisioned infrastructure
- EventBridge charges only for events actually sent
- CloudTrail consolidation reduces duplicate logging costs
The customer saw >45% cost reduction compared to their prior SIEM-based ingestion model.
✔ Scales Automatically to New Accounts
When new AWS accounts are created, they are automatically onboarded through AWS Organizations — no manual configuration required.
✔ Minimal Operational Burden
The central team no longer maintains scripts, schedulers, or account-specific monitoring setups. Everything is automated.
Example: How This Helped the Customer
Within weeks of implementation:
- All 270 accounts were sending filtered events into the central logging pipeline
- The compliance team could run unified audit reports within minutes
- Critical IAM activities were being flagged instantly
- The customer eliminated thousands of euros in previously wasted monthly costs
- Quarterly audit cycles were reduced from “weeks of manual work” to “a few hours”
This event-driven approach became a strategic enabler — giving the organisation the visibility it needed without the traditional cost and complexity of multi-account logging.
Conclusion
Centralising logging and monitoring across hundreds of AWS accounts doesn’t have to be expensive or complicated.
By leveraging AWS-native, serverless, event-driven services, enterprises can achieve:
- Real-time visibility
- Strong compliance posture
- Significant cost savings
- Automated scalability
- Reduced operational overhead
For EU organisations operating at scale, this model provides a modern, compliant, and cost-optimised foundation for cloud governance.
If your organisation faces similar challenges, our team can help you design and deploy a solution tailored to your compliance requirements, operational structure, and budget.


